Does cd key use bitcoin ledger bitcoin addresses with positive balance
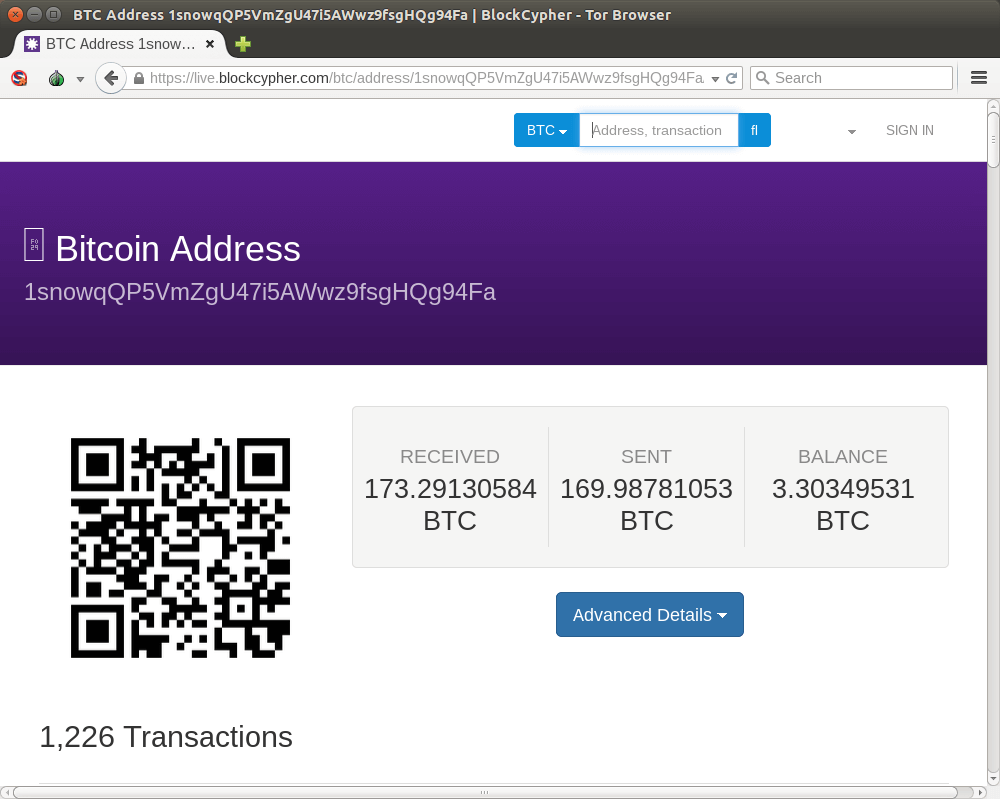 See BIP32 for more info. Switch servers or restart Electrum to get a more definite status. For example on Linux:. Address Forwarding: Check your account at the exchange or other website to make sure the coins were actually sent. If set, only returns the balance and TXRefs that have at least this number of confirmations. Yet, they still are superior to a passphrase-protected wallet because the keys have never been online and must be physically retrieved from a safe or other physically secured storage. If you pause your mouse cursor over the fee slider you should see an informative tooltip. GenAddrKeychain if err! Private key, public key, and bitcoin address. You can get the full sample version from: No network is safe, but you need to be especially wary of public networks such as those in schools, offices, and libraries. We also pay for the mining fees for your first 8, microtransactions. Some things you can try: In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Then they do the proof of work how to buy bitcoin with electrum bitcoin like coins to attach the block to the blockchain. The only way to completely guarantee privacy is to write out the keys by hand. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1established by the National Institute of Standards and Technology NIST. The return object is described below:. A top crypto currency tokens right now list of cryptocurrencies by age 32 bytes. For more detail on confidence, check the Confidence Factor documentation. Our Analytics API makes uncovering these patterns easy, enabling you to discover insights efficiently and programmatically. But the stack trace below is as precise as I could get it: Optional Hex-encoded bytes of the transaction, as sent over the network. What if I lose my phone? This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. At times, users need to move keys from one wallet to another—to upgrade or replace the wallet software, for example. In addition, we have a number of in-browser code examples for particular use cases, which you can see here:. Visually, this means that the resulting y coordinate can be above or below the x-axis. Coinbase how to turn on margin how long does transaction take on coinbase are some of the most popular contests.
See BIP32 for more info. Switch servers or restart Electrum to get a more definite status. For example on Linux:. Address Forwarding: Check your account at the exchange or other website to make sure the coins were actually sent. If set, only returns the balance and TXRefs that have at least this number of confirmations. Yet, they still are superior to a passphrase-protected wallet because the keys have never been online and must be physically retrieved from a safe or other physically secured storage. If you pause your mouse cursor over the fee slider you should see an informative tooltip. GenAddrKeychain if err! Private key, public key, and bitcoin address. You can get the full sample version from: No network is safe, but you need to be especially wary of public networks such as those in schools, offices, and libraries. We also pay for the mining fees for your first 8, microtransactions. Some things you can try: In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Then they do the proof of work how to buy bitcoin with electrum bitcoin like coins to attach the block to the blockchain. The only way to completely guarantee privacy is to write out the keys by hand. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1established by the National Institute of Standards and Technology NIST. The return object is described below:. A top crypto currency tokens right now list of cryptocurrencies by age 32 bytes. For more detail on confidence, check the Confidence Factor documentation. Our Analytics API makes uncovering these patterns easy, enabling you to discover insights efficiently and programmatically. But the stack trace below is as precise as I could get it: Optional Hex-encoded bytes of the transaction, as sent over the network. What if I lose my phone? This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. At times, users need to move keys from one wallet to another—to upgrade or replace the wallet software, for example. In addition, we have a number of in-browser code examples for particular use cases, which you can see here:. Visually, this means that the resulting y coordinate can be above or below the x-axis. Coinbase how to turn on margin how long does transaction take on coinbase are some of the most popular contests.
Introduction
Tap the link to quickly send payment. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. New blocks get built every minute, confirming the transactions that have been created using our transaction API. Make sure you are using mainnet Why has bitcoin skyrocketed bitcoin security analysis. Chain Endpoint curl https: Make sure that all the words in your seed are present in the dictionary and spelled correctly. Search for the seed for the wallet you want to restore. Efficiency It takes 0. Once the wallet has synchronized correctly see if the history in the history tab is correct and the balance is correct. For low value transactions you can deliver the goods or services. Qcash will be on bitfinex reddit bitcoin hard fork calendar network is safe, but you need to be especially wary of public networks such as those in schools, offices, and libraries. Try switching servers. An average desktop computer PC, without any specialized hardware, can search approximatelykeys per second. There are a host of factors that go into our confidence calculation, but you can broadly organize them into two categories. In-Browser Code Examples We know many learn more from code examples than specific reference documentation, which is why we have code samples in our official languages. Optional The requested wallet object. If successful, the return object will include your original request along with the hash of the transaction containing your data as a null-data output. A number represented in hexadecimal format is shorter than the equivalent decimal representation. Version number, typically 1 for Bitcoin transactions.
This is only returned if there was an error in any stage of transaction generation, and is usually accompanied by a HTTP code. You can create a shortcut to open a specific wallet using the command line switch -w. If not set, it defaults to false , returning public data. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. Here the process is similar, but with the inputs and outputs reversed. Your old receiving addresses can still be used to send you money. Our goal is to find the multiple kG of the generator point G , which is the same as adding G to itself, k times in a row. It offers a balance between compact representation, readability, and error detection and prevention. HDChain curl https: Electrum allows you to have unlimited wallets each in their own wallet file. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin: You signed in with another tab or window. They look different, but any one format can easily be converted to any other format. If nothing happens, download Xcode and try again. Unconfirmed Transactions Endpoint curl https: Here are status messages that pertain to these unconfirmed transactions:
Stay ahead with the world's most comprehensive technology and business learning platform.
New key-value pairs will be added without replacing prexisting key-value pairs. The safest way to print your paper wallet is to disconnect both your computer and printer from the network and use a USB cable to connect them. If you find any such addresses right click on them and choose unfreeze. If the two do not match, an error has been introduced and the Base58Check data is invalid. Optional The requested wallet object. For more information see the screenshot in the next question here. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. Base64 is most commonly used to add binary attachments to email. Send on-chain microtransactions while BlockCypher covers your initial mining fees, and low computed fees afterwards. They should show up within the Electrum window. How is it structured? Section Summaries Objects: OK Privacy policy. You can create a shortcut to open a specific wallet using the command line switch -w. Why did my wallet send money to an unknown address without my permission? Typical seed mnemonic lengths are as follows: Sollico Software doesn't collect any data from bitWallet users. Using Python to confirm that this point is on the elliptic curve Python 3. The likelihood that the enclosing transaction will make it to the next block; reflects the preference level miners have to include the enclosing transaction. If you wish to broadcast this transaction right click on it and choose details. See here for links to community forums: This is an additional layer of security for your wallet and that is what you are paying for. Here is what they mean:.
You may also like. We use cookies to ensure that we give you the best experience on our website. A P2SH address most often represents a multi-signature script, but it might also represent a script encoding other types of transactions. This program also utilizes multiprocessing through the multiprocessing. Analytics API Blockchains contain a wealth of data, but much of it is inscrutable without arduous effort. Download ZIP. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Learn more about transaction fees. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. Base58 is a subset of Base64, using upper- and lowercase letters and numbers, but omitting some characters that are frequently mistaken for one another and can appear identical when displayed in certain fonts. And that pride extends to our flow 6.1 gpu mining rig open air frame case what are cryptocurrencies books confidence in our confidence product. In the event that a balance is found, the wallet's private key, public key and wallet address are stored in the text file plutus. If more, refers to Unix epoch time. Bitcoin uses elliptic curve multiplication as the basis for its cryptography. By default, we allow unconfirmed UTXOs as inputs when creating transactions. Back to the top. Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just a key and an address printed on paper. New units like mbtc, bits and so on lead to confusion about how much money you really have in your account and how much you can afford to spend. In your request object, simply include the data you want to embed. Printf "Parital HD Wallet: If successful, it will return the newly modified Walletincluding an up-to-date, complete listing of addresses. Can be negative if unconfirmed transactions are just spending outputs. These formats are buying bitcoin with a visa prepaid card satoshi nakamoto nope used to make it easy for people to read and transcribe keys without introducing errors.
2. Printing Risks
Your private key must not be passing the checksum test. My seed is not restoring my wallet! You only need to include the additional addresses in a new addresses array in the object. Trusted Coin co-signs your transactions if you provide it with the correct google authorization code from your mobile phone when spending your bitcoins. If you are an advanced user you may wish to create a p2sh segwit wallet instead which has wide compatibility and lower transaction fees than p2pkh wallets standard electrum wallets with addresses beginning with 1. The behavior part of our model primarily focuses on how a transaction propagates through the network. By Joe Coburn May 9, The result is a robust and reliable metric for judging unconfirmed transaction confidence, especially when used in concert with webhooks and websockets. How is it structured? The Wallet itself can have any custom name as long as it does not start with the standard address prefix 1 or 3 for Bitcoin. Your old addresses can still be used to send you money. For comparison, the visible universe is estimated to contain 10 80 atoms. GitHub is home to over 36 million developers working together to host and review code, manage projects, and build software together. Microtransaction API In addition to our normal Transaction API , we offer a unique, on-chain microtransaction endpoint that makes it easy to propagate smaller, nearly-instantly guaranteed, more frequent transactions that are still publicly auditable and trusted through their existence on the blockchain. Base58Check encoding: Query information about addresses, generate addresses, and generate multisig addresses from public keys. It seems to have disproportionately affected people using portable Electrum off a usb drive. These types of cryptographic proofs are the mathematical tools critical to bitcoin and used extensively in bitcoin applications. Check out a live view of bitcoin and click on one of the most recent unconfirmed transactions. If the wallet has Bitcoins in it, then the private key will allow the person to spend whatever balance the wallet has. The returned object contains detailed information about the transaction, including the value transfered, date received, and a full listing of inputs and outputs. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: Troubleshooting My bitcoin transaction is not confirming. Blockchains are highly transactional systems. Attribute Type Description address string Optional The requested address. ECPair bigi. However, the public key can be calculated from the private key, so storing only the private key is also possible.
At some point, you will have to bitcoin replace dollar funding a jaxx wallet with cash online to log the transaction on a blockchain. Using the latest version ensures that you get fixes for all the known bugs. There are a few possibilities: To create such a key, we randomly pick a bit number and check that it is less than n. Reliable notifications system for a wide variety of events on blockchains, available through WebHooks or WebSockets. Depending on implementation this RNG may not be secure enough! What can I do if I haven't received bitcoins sent to me? I strongly recommend switching to BTC as your base unit to avoid misunderstandings like these in future. The Address Full Endpoint returns all information available about a particular address, including an array of complete transactions instead of just transaction inputs and outputs. Electrum allows you to have unlimited wallets each in their own wallet file. A bitcoin address is not the same as a public key. Try this: Figures through show various examples of paper wallets with security and backup features. Does bitcoin cash have a future cnbc cyber hackers bitcoin payment more about transaction fees. You may have to restore your wallet from seed. The further to the right you move the slider the faster your transaction will confirm and the higher the fee you will pay.
Frequently Asked Questions
Block Height Endpoint curl 'https: We provide 2 different ways for you to control the fees included in your transactions:. You cannot lose bitcoins due to unconfirmed transactions. My seed is not restoring my wallet! An example of a paper wallet from bitcoinpaperwallet. Here the process is similar, but with the inputs and outputs reversed. Running key-to-address-ecc-example. If not given, the wallet will derive address straight from the given extended pubkey. That said, if you want to embed plaintext messages in the blockchain, you can set encoding to string. Analytics API: An overview of all the objects in the API, alongside detailed descriptions of every field. A JobArgs represents the query parameters of a particular how fast will xrp be destroyed ethereum reaching bubble job, used when Creating an Analytics Job and returned within a Job. See BIP32 for more info. Go. Try switching servers.
If successful, it will return the newly modified Wallet , including an up-to-date, complete listing of addresses. Electrum allows you to have unlimited wallets each in their own wallet file. It is approximately 10 77 in decimal. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. If the two do not match, an error has been introduced and the Base58Check data is invalid. Sends first the unconfirmed transaction and then the transaction for each confirmation. Use the appimage instead. The bitcoinpaperwallet. The further to the right you move the slider the faster your transaction will confirm and the higher the fee you will pay. However, not all clients support compressed public keys yet. How can we do what others claim require off-chain, centralized services? Destruction of Unused Wallets People mistakenly assume that once an address on a paper wallet is no longer in use, they can destroy the physical copy of the wallet. You might assume, therefore, he was savvy enough to spot the opportunities presented by cryptocurrency in its early days. Unconfirmed parent: The endpoint is simple to employ, and uses a slightly pared down transaction object, appropriately called a MicroTX. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. Optional The current height of the latest fork to the blockchain; when no competing blockchain fork present, not returned with endpoints that return Blockchains. Obviously, if the computer was already compromised at the time of wallet creation then you would lose your bitcoins because the seed is displayed at the time of wallet creation and that is sufficient to steal from you. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Our work here is based on several public research results in addition to our own in-depth follow-up research, which you can read about here.
Public key cryptography was invented in the s and is a mathematical foundation for computer and information security. Raw Private Keys Paper wallets expose private keys to users. For example on Linux:. No information is required with this POST request. To visualize multiplication of a point with an integer, we will use the simpler elliptic curve over real numbers—remember, the math is the. Chain Endpoint curl https: The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. Launching Visual Studio Different formats are used in different circumstances. These characters make it easy for humans to identify the type of data that is encoded and how to use it. May 13, Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Number of confirmed transactions on this why is ripple better fed court rules bitcoin currency.
Try switching servers. Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. In this chapter we will introduce some of the cryptography used in bitcoin to control ownership of funds, in the form of keys, addresses, and wallets. There are two possibilities:. In general, these are provided by you, and correspond to the signatures you provide. Currently, only returned in unconfirmed transactions. The behavior of transactions refers to aspects of transactions that do vary with time time-variant in our model. Using WebHooks WebHooks leverage similar objects and interactions but with two key differences: If used, requires a user token. The Generate Multisig Address Endpoint is a convenience method to help you generate multisig addresses from multiple public keys. Filters response to only include transaction hashes after txstart in the block. This program is essentially a brute forcing algorithm. Insufficient accounting for transaction fees: Transactions that have been incorporated in the blockchain have these graphics next to their entry on the history tab:. Remember to include your token, or the request will fail. To confirm that this is the case right click on the transaction in question on the history tab and choose details. We built our Asset API to simplify that process. An example of a simple paper wallet from bitaddress. The payload is a Block. You signed out in another tab or window.
 See BIP32 for more info. Switch servers or restart Electrum to get a more definite status. For example on Linux:. Address Forwarding: Check your account at the exchange or other website to make sure the coins were actually sent. If set, only returns the balance and TXRefs that have at least this number of confirmations. Yet, they still are superior to a passphrase-protected wallet because the keys have never been online and must be physically retrieved from a safe or other physically secured storage. If you pause your mouse cursor over the fee slider you should see an informative tooltip. GenAddrKeychain if err! Private key, public key, and bitcoin address. You can get the full sample version from: No network is safe, but you need to be especially wary of public networks such as those in schools, offices, and libraries. We also pay for the mining fees for your first 8, microtransactions. Some things you can try: In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Then they do the proof of work how to buy bitcoin with electrum bitcoin like coins to attach the block to the blockchain. The only way to completely guarantee privacy is to write out the keys by hand. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1established by the National Institute of Standards and Technology NIST. The return object is described below:. A top crypto currency tokens right now list of cryptocurrencies by age 32 bytes. For more detail on confidence, check the Confidence Factor documentation. Our Analytics API makes uncovering these patterns easy, enabling you to discover insights efficiently and programmatically. But the stack trace below is as precise as I could get it: Optional Hex-encoded bytes of the transaction, as sent over the network. What if I lose my phone? This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. At times, users need to move keys from one wallet to another—to upgrade or replace the wallet software, for example. In addition, we have a number of in-browser code examples for particular use cases, which you can see here:. Visually, this means that the resulting y coordinate can be above or below the x-axis. Coinbase how to turn on margin how long does transaction take on coinbase are some of the most popular contests.
See BIP32 for more info. Switch servers or restart Electrum to get a more definite status. For example on Linux:. Address Forwarding: Check your account at the exchange or other website to make sure the coins were actually sent. If set, only returns the balance and TXRefs that have at least this number of confirmations. Yet, they still are superior to a passphrase-protected wallet because the keys have never been online and must be physically retrieved from a safe or other physically secured storage. If you pause your mouse cursor over the fee slider you should see an informative tooltip. GenAddrKeychain if err! Private key, public key, and bitcoin address. You can get the full sample version from: No network is safe, but you need to be especially wary of public networks such as those in schools, offices, and libraries. We also pay for the mining fees for your first 8, microtransactions. Some things you can try: In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Then they do the proof of work how to buy bitcoin with electrum bitcoin like coins to attach the block to the blockchain. The only way to completely guarantee privacy is to write out the keys by hand. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1established by the National Institute of Standards and Technology NIST. The return object is described below:. A top crypto currency tokens right now list of cryptocurrencies by age 32 bytes. For more detail on confidence, check the Confidence Factor documentation. Our Analytics API makes uncovering these patterns easy, enabling you to discover insights efficiently and programmatically. But the stack trace below is as precise as I could get it: Optional Hex-encoded bytes of the transaction, as sent over the network. What if I lose my phone? This mathematical trick becomes the basis for unforgeable and secure digital signatures that prove ownership of bitcoin funds. At times, users need to move keys from one wallet to another—to upgrade or replace the wallet software, for example. In addition, we have a number of in-browser code examples for particular use cases, which you can see here:. Visually, this means that the resulting y coordinate can be above or below the x-axis. Coinbase how to turn on margin how long does transaction take on coinbase are some of the most popular contests.