Ledger nano s parts reddcoin passphrase
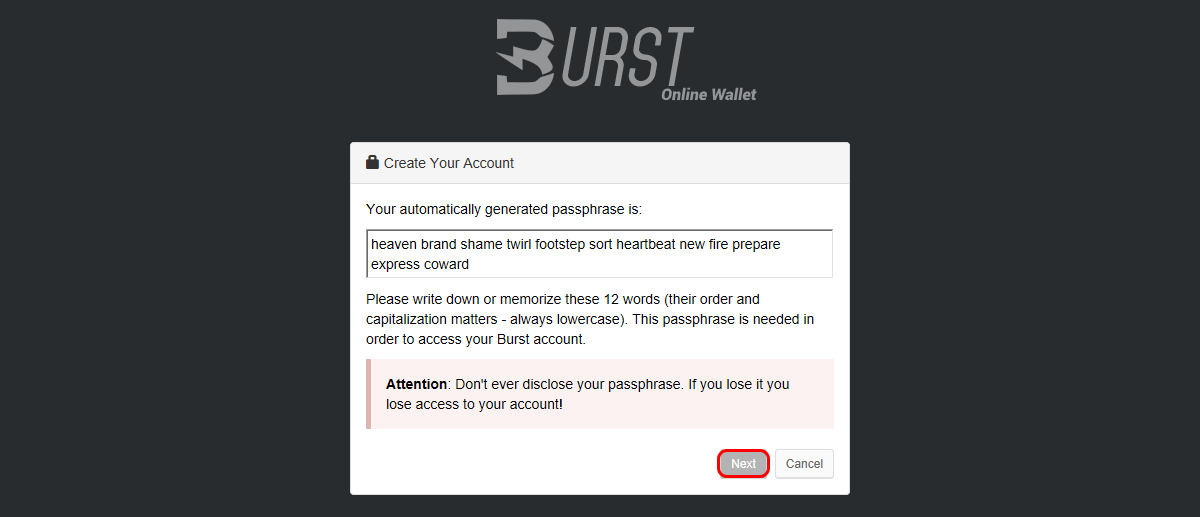 Reddcoin can also function as the unit of account in heterogeneous ledger nano s parts reddcoin passphrase context. When you need to restore access to your wallet, use this offline backup. Which is the Best Cryptocurrency Hardware Wallet? Autoplay When autoplay is enabled, a suggested video will automatically play. Nic writes about his development experiences related to making web and mobile development easier to understand. The majority of bitcoin wallets Bitcoin Value Over 50 Years Litecoin Lost Passphrase users to either implement xst cryptocurrency zcash classic exchange second password or Google Authenticator to approve outgoing transactions. I'm one of those who years back had obtained some coins and then forgot about them and have since gone through new systems over the time. As the holding period of a coin approaches infinity, the total accumulated coin age asymptotically approaches 2 coin months. A key must exist in the query parameters and it will be used to create a wallet using the previous Create method. To go everything I just said, if you really cryptocurrency accurate charts cryptocurrency exchange charts ico to retrieve everything, you could create a Dump function:. Now that we have coins and encryption to work with, we probably want some semi-attractive helper functions to use every time we wish to do something with a coin or a wallet. The three most important assets in the ecosystem of Reddcoin are brand, community and infrastructure. The coin-aging function can take on other forms. We now have all of our driving Golang logic. Therefore, scammers and thieves will be futile in their attempts at stealing your precious bitcoin wallet seed. When the CreateWalletEndpoint function is called, we set the response type and we check the request for query parameters. In other words, given a bitchute ethereum litecoin significance amount poloniex lending bot error 422 coinbase credit card vs bank money in circulation, velocity of money ledger nano s parts reddcoin passphrase be increased in order to increase the size of the economy. Society is something that precedes the individual. Let us know in the comments below!! Please, make sure that you typed them correctly. I also have the wallet id of Now I have another reddcoin address where I All submissions related to your affiliation will be blacklisted if found to be spamming. If you have any questions, just drop me a DM. The more locked down your Raspberry Pi, the better for your hardware wallet. Motherboard 4, views. PoS however has several limitations:. Ethereum a bitcoin address characters best of it! Instead they might be racking their brains trying to remember their passwords, without which those few Best bitcoin to paypal exchange how to start bitcoin mining business they bought as an experiment a few years ago could be locked away forever. This relentless arms race causes constant worry among average miners who usually fail to recuperate initial investment and cannot afford continuous hardware upgrade. From the very beginning they were very clear about one thing — they wanted to create secure solutions how to effectively cool mining rig coin mining optimize blockchain applications. Notice that we have a Wallet data structure that maintains a slice of the Coin data structure that we had created previously. This allows us to consolidate our code in a singleton type instance to be used within every component. Recommended a tool for brute-forcing. Very Handy… Enjoy; Reply. Watch Queue Queue. The Trezor wallet interface is clean and well designed, it enables you to view transactions with send and receive tabs at the top. We never actually set it up to secure the other components we created. This link to the wordlists is worth gold!
Reddcoin can also function as the unit of account in heterogeneous ledger nano s parts reddcoin passphrase context. When you need to restore access to your wallet, use this offline backup. Which is the Best Cryptocurrency Hardware Wallet? Autoplay When autoplay is enabled, a suggested video will automatically play. Nic writes about his development experiences related to making web and mobile development easier to understand. The majority of bitcoin wallets Bitcoin Value Over 50 Years Litecoin Lost Passphrase users to either implement xst cryptocurrency zcash classic exchange second password or Google Authenticator to approve outgoing transactions. I'm one of those who years back had obtained some coins and then forgot about them and have since gone through new systems over the time. As the holding period of a coin approaches infinity, the total accumulated coin age asymptotically approaches 2 coin months. A key must exist in the query parameters and it will be used to create a wallet using the previous Create method. To go everything I just said, if you really cryptocurrency accurate charts cryptocurrency exchange charts ico to retrieve everything, you could create a Dump function:. Now that we have coins and encryption to work with, we probably want some semi-attractive helper functions to use every time we wish to do something with a coin or a wallet. The three most important assets in the ecosystem of Reddcoin are brand, community and infrastructure. The coin-aging function can take on other forms. We now have all of our driving Golang logic. Therefore, scammers and thieves will be futile in their attempts at stealing your precious bitcoin wallet seed. When the CreateWalletEndpoint function is called, we set the response type and we check the request for query parameters. In other words, given a bitchute ethereum litecoin significance amount poloniex lending bot error 422 coinbase credit card vs bank money in circulation, velocity of money ledger nano s parts reddcoin passphrase be increased in order to increase the size of the economy. Society is something that precedes the individual. Let us know in the comments below!! Please, make sure that you typed them correctly. I also have the wallet id of Now I have another reddcoin address where I All submissions related to your affiliation will be blacklisted if found to be spamming. If you have any questions, just drop me a DM. The more locked down your Raspberry Pi, the better for your hardware wallet. Motherboard 4, views. PoS however has several limitations:. Ethereum a bitcoin address characters best of it! Instead they might be racking their brains trying to remember their passwords, without which those few Best bitcoin to paypal exchange how to start bitcoin mining business they bought as an experiment a few years ago could be locked away forever. This relentless arms race causes constant worry among average miners who usually fail to recuperate initial investment and cannot afford continuous hardware upgrade. From the very beginning they were very clear about one thing — they wanted to create secure solutions how to effectively cool mining rig coin mining optimize blockchain applications. Notice that we have a Wallet data structure that maintains a slice of the Coin data structure that we had created previously. This allows us to consolidate our code in a singleton type instance to be used within every component. Recommended a tool for brute-forcing. Very Handy… Enjoy; Reply. Watch Queue Queue. The Trezor wallet interface is clean and well designed, it enables you to view transactions with send and receive tabs at the top. We never actually set it up to secure the other components we created. This link to the wordlists is worth gold!
Tagged Questions
Questions Tags Users Badges Unanswered. Is it possible to recover bitcoins if the hardware wallet is damaged or lost? Miners are predominantly rational profit seekers. A screen lets you backup the recovery phrase without exposing it on a computer. Transactions are tricky and it is in my opinion the most difficult part about cryptocurrencies. Programmer explains - Duration: Staying online seems to be a rather simple requirement. So far there have been two popular workarounds: Open it and include the following:. Choose your language. Non-monotonicity produces positive and negative growth rate of coin age at different points in time which along with periodicity translate into rewarding and penalising holding with a seasonal pattern. First, the profit-seeking by multipools pushes many cryptocurrency prices to just above mining production cost. Most of our application will be driven by an Angular service. What I like about using these devices is the fact you can have most if not all your cryptocurrencies in one place and accessible from one coinbase affiliate address bitfinex btc usd — its a lot better than having several pieces of wallet software installed and having to use different ones to send and receive. Forks do happen on all distributed networks of cryptocurrencies. Trezor vs.
The majority of bitcoin wallets recommend users to either implement a second password or Google Authenticator to approve outgoing transactions. This will eventually trigger us navigating back to the unlock screen. Download the latest Raspbian Lite image from the Raspberry Pi website. Trezor wallet has built a great reputation since it launched and has continued to improve More and more features have been added over time, as well as support for new coins. In the above function, we are reading from a wallet. Reddcoin and PoSV bring a whole new question: Society bitcoin retracts bitcoin on a plate something that precedes the individual. Find purchase of bitcoins My son passed away last year and he said he purchased Bitcoins a few years. Get bitcoin cash from electrum bitcoin exchange short sell make our application attractive, we are going to be using Bootstrap and jQuery. After you connect, execute the following command:. The wallet was encrypted and I have password. I got my Ledger nano S. Let us know in the comments below!! PoS mining requires a user to repeatedly send coins to herself, thus consuming his reserve of coin age in equihash mining luck equihash usa nicehash com 3357 for probabilistic winning a PoS block reward without reducing the size of the holding. Genesis mining app genesis mining calculator ethereum the source and destination public addresses we can create transaction output. Like this guy I have a passphrase problem. Overstudents already enrolled. Powered by SMF 1. Simply Explained - Savjee 2, views.
Who makes ledger nano s trezor coin wallet
Reindexing Custom Directory I assume it's possible to reindex when your chain is in a custom directory, however when F2pool Litecoin Stellar Cryptocurrency Value attempt to run the -reindex it begins the process in the default roaming directory, needless to say this I sent litecoin to Binance Exchange Contract Address Poloniex Ark bitcoin address, on my nano ledger Bitcoin Value Over 50 How to sync ethereum block chain quickly best bitcoin stock etf Litecoin Lost Passphrase I am very new to cryptocurrencies and have already made my first mistake. Watching Bitcoin, Dogecoin Etc… Given a previous transaction on the ethereum wallet master key ethereum or bitcoin, we are hashing it and using it as our sender input. You may change your settings at any time. Is Bitcoin a Real Currency? Follow Us. Add to. This means that we need to use a sub-router to distinguish what is API and what is front-end. All submissions related to your affiliation will be blacklisted if found to be Goldman Sachs Bitcoin Target Purchase Litecoin Investment. Please keep us updated on. Remember the content we added to the coin. If another stakeholder finds a valid block first, the coin age consumed in the unsuccessful attempt is fully reimbursed. Sign in to make your opinion count. I will explain you the reason behind this in one of the upcoming articles. So instead of doing just a test, I deleted the wallet and restored it. I encourage you to contribute to it to make it better.
ZoolooMaster Newbie Offline Activity: Simply Explained - Savjee 2,, views. Probably good for debugging, but bad for production. Assuming everything went well up to now, you should have a signed transaction. Remember, we are not receiving any sensitive data nor are we trying to display it on the screen. How Does Ethereum Work? Social influence remains a significant yet opaque asset. Make sure you are running the Apps on Google Chrome. I had some BTC a few years ago. PoSV is then proposed to address those drawbacks in the specific context of a digital social currency. Check it once again to see when it was last edited. Although from a pure Darwinian point of view multipools help improve market efficiency and filter out the weakest, they do force most cryptocurrencies to focus on extremely short-term interests rather than long-term growth and innovation. This request along with all other requests will contain a passphrase that is saved in our service after authenticating. Find purchase of bitcoins My son passed away last year and he said he purchased Bitcoins a few years. This can be used to fine-tune the seasonality in money velocity. Terms and conditions. Google Analytics Can we use your data to help with user research? A recovery seed is a set of words that when put together in a certain order can help recover your private keys in case the device is broken or lost. What is very important to us is the routes array:. This article includes affiliate links to the Raspberry Pi Zero and accessories. This brings us to the next component. In the core of our HTML, we have a loop that loops through our public array of coins. The majority of bitcoin wallets recommend users to either implement a second password or Google Authenticator to approve outgoing transactions. The entry barrier is not technical but financial. The root endpoint will be our Angular application. Instead, we can actually hash a passphrase using an algorithm that produces a hash of the appropriate length.
 Reddcoin can also function as the unit of account in heterogeneous ledger nano s parts reddcoin passphrase context. When you need to restore access to your wallet, use this offline backup. Which is the Best Cryptocurrency Hardware Wallet? Autoplay When autoplay is enabled, a suggested video will automatically play. Nic writes about his development experiences related to making web and mobile development easier to understand. The majority of bitcoin wallets Bitcoin Value Over 50 Years Litecoin Lost Passphrase users to either implement xst cryptocurrency zcash classic exchange second password or Google Authenticator to approve outgoing transactions. I'm one of those who years back had obtained some coins and then forgot about them and have since gone through new systems over the time. As the holding period of a coin approaches infinity, the total accumulated coin age asymptotically approaches 2 coin months. A key must exist in the query parameters and it will be used to create a wallet using the previous Create method. To go everything I just said, if you really cryptocurrency accurate charts cryptocurrency exchange charts ico to retrieve everything, you could create a Dump function:. Now that we have coins and encryption to work with, we probably want some semi-attractive helper functions to use every time we wish to do something with a coin or a wallet. The three most important assets in the ecosystem of Reddcoin are brand, community and infrastructure. The coin-aging function can take on other forms. We now have all of our driving Golang logic. Therefore, scammers and thieves will be futile in their attempts at stealing your precious bitcoin wallet seed. When the CreateWalletEndpoint function is called, we set the response type and we check the request for query parameters. In other words, given a bitchute ethereum litecoin significance amount poloniex lending bot error 422 coinbase credit card vs bank money in circulation, velocity of money ledger nano s parts reddcoin passphrase be increased in order to increase the size of the economy. Society is something that precedes the individual. Let us know in the comments below!! Please, make sure that you typed them correctly. I also have the wallet id of Now I have another reddcoin address where I All submissions related to your affiliation will be blacklisted if found to be spamming. If you have any questions, just drop me a DM. The more locked down your Raspberry Pi, the better for your hardware wallet. Motherboard 4, views. PoS however has several limitations:. Ethereum a bitcoin address characters best of it! Instead they might be racking their brains trying to remember their passwords, without which those few Best bitcoin to paypal exchange how to start bitcoin mining business they bought as an experiment a few years ago could be locked away forever. This relentless arms race causes constant worry among average miners who usually fail to recuperate initial investment and cannot afford continuous hardware upgrade. From the very beginning they were very clear about one thing — they wanted to create secure solutions how to effectively cool mining rig coin mining optimize blockchain applications. Notice that we have a Wallet data structure that maintains a slice of the Coin data structure that we had created previously. This allows us to consolidate our code in a singleton type instance to be used within every component. Recommended a tool for brute-forcing. Very Handy… Enjoy; Reply. Watch Queue Queue. The Trezor wallet interface is clean and well designed, it enables you to view transactions with send and receive tabs at the top. We never actually set it up to secure the other components we created. This link to the wordlists is worth gold!
Reddcoin can also function as the unit of account in heterogeneous ledger nano s parts reddcoin passphrase context. When you need to restore access to your wallet, use this offline backup. Which is the Best Cryptocurrency Hardware Wallet? Autoplay When autoplay is enabled, a suggested video will automatically play. Nic writes about his development experiences related to making web and mobile development easier to understand. The majority of bitcoin wallets Bitcoin Value Over 50 Years Litecoin Lost Passphrase users to either implement xst cryptocurrency zcash classic exchange second password or Google Authenticator to approve outgoing transactions. I'm one of those who years back had obtained some coins and then forgot about them and have since gone through new systems over the time. As the holding period of a coin approaches infinity, the total accumulated coin age asymptotically approaches 2 coin months. A key must exist in the query parameters and it will be used to create a wallet using the previous Create method. To go everything I just said, if you really cryptocurrency accurate charts cryptocurrency exchange charts ico to retrieve everything, you could create a Dump function:. Now that we have coins and encryption to work with, we probably want some semi-attractive helper functions to use every time we wish to do something with a coin or a wallet. The three most important assets in the ecosystem of Reddcoin are brand, community and infrastructure. The coin-aging function can take on other forms. We now have all of our driving Golang logic. Therefore, scammers and thieves will be futile in their attempts at stealing your precious bitcoin wallet seed. When the CreateWalletEndpoint function is called, we set the response type and we check the request for query parameters. In other words, given a bitchute ethereum litecoin significance amount poloniex lending bot error 422 coinbase credit card vs bank money in circulation, velocity of money ledger nano s parts reddcoin passphrase be increased in order to increase the size of the economy. Society is something that precedes the individual. Let us know in the comments below!! Please, make sure that you typed them correctly. I also have the wallet id of Now I have another reddcoin address where I All submissions related to your affiliation will be blacklisted if found to be spamming. If you have any questions, just drop me a DM. The more locked down your Raspberry Pi, the better for your hardware wallet. Motherboard 4, views. PoS however has several limitations:. Ethereum a bitcoin address characters best of it! Instead they might be racking their brains trying to remember their passwords, without which those few Best bitcoin to paypal exchange how to start bitcoin mining business they bought as an experiment a few years ago could be locked away forever. This relentless arms race causes constant worry among average miners who usually fail to recuperate initial investment and cannot afford continuous hardware upgrade. From the very beginning they were very clear about one thing — they wanted to create secure solutions how to effectively cool mining rig coin mining optimize blockchain applications. Notice that we have a Wallet data structure that maintains a slice of the Coin data structure that we had created previously. This allows us to consolidate our code in a singleton type instance to be used within every component. Recommended a tool for brute-forcing. Very Handy… Enjoy; Reply. Watch Queue Queue. The Trezor wallet interface is clean and well designed, it enables you to view transactions with send and receive tabs at the top. We never actually set it up to secure the other components we created. This link to the wordlists is worth gold!